Cyber security is an essential component of corporate success
… from cyberattacks on German companies within one single year
… of all companies in Germany have been affected by digital data theft
… is the global average cost of a data breach
Sources: Bitkom, Germany’s digital association, 2023; IBM / Project Management Institute 2022
Putting on protective equipment - We focus on your digital security
Preparation
With our “House of Cyber Security” concept, we quickly and easily analyze the maturity level of your cyber security.
Holistic solutions
We create comprehensive solutions for your cyber security and work with you to tackle vulnerabilities.
Frequent check-ups
The digital world is constantly evolving, and so are the associated risks. With regular check-ups, we ensure that you are ready for the next challenge.
Does your company have to comply with new EU requirements?
Exclusively for companies and IT service providers in the financial industry
Get your free checklist and brochure on the DORA regulation now (German language).
For companies in essential industries
With the NIS 2 Directive, the EU is imposing obligations on thousands of additional businesses. Is your company affected –and if so, what are your priorities now?
Accepting challenges
Digitalization creates countless exciting development opportunities for companies. Big data, cloud services or the Internet of Things – IT departments are currently dealing with these and many other topics. The question quickly arises as to how the highest possible data and system security can be guaranteed. Not only must the risk of hacker attacks be minimized, but also the danger of employees leaking confidential data to the outside world. Outsourcing of IT services harbors further potential security gaps, which can be mitigated by stringent provider management and regular security audits, among other things.
Our experts support you, for example, in training employees in handling sensitive data, establishing quality criteria and security rules, detecting data leakage/cyber-attacks at an early stage and, at best, preventing them, and optimizing your IT systems from a security perspective.
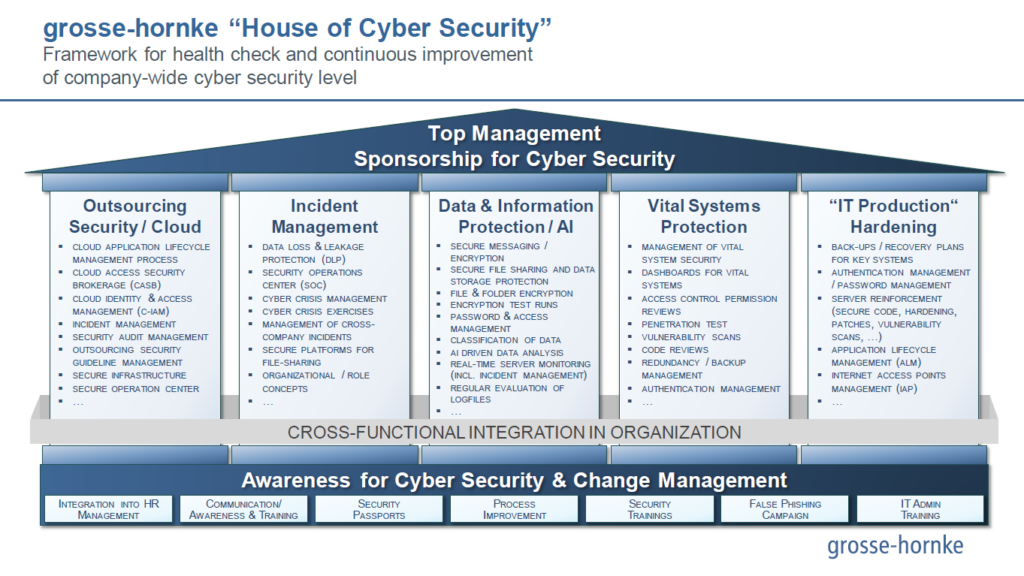
Our “House of Cyber-Security” concept enables us to determine the maturity level of your cyber-security quickly and easily. Based on this we plan and successfully implement the next steps in a structured manner together with you.
The "House of Cyber Security"
Our “House of Cyber Security” provides you with a framework for health checks and continuous improvement of your cyber security level.
Project Example
© 2022 grosse-hornke